SolarWinds Attack Is a Cautionary Tale for Hardware and Its Supply Chain
By: John Hallman
The recent SolarWinds hacking incident that left many fortune-500 companies and US government networks exposed is an interesting cautionary tale for unchecked software and hardware supply chain security vulnerabilities.


The highly sophisticated software supply chain attack occurred in the SolarWinds Orion IT monitoring system. This system, used by over 33,000 companies, monitors performance across multiple networks. In early March of 2020, SolarWinds unintentionally sent a certified binary software update that included malicious code to 18,000 clients. The hacked code created a backdoor to companies’ IT systems that allowed even more malware to be installed allowing the hackers to spy on these companies. The backdoor communicated via HTTP to third-party servers and uses multiple blocklists to identify forensic and anti-virus tools running as processes, services, and drivers. This attack meant that highly confidential information was exposed and could have resulted in complete control of the systems being lost.
Although this attack happened through software, hardware and its supply chain are susceptible to comparable attack scenarios. During pre-IC fabrication a backdoor could be inserted at the time of design or within integrated IP. It could even occur during mask or silicon modification. After IC fabrication, malicious logic could find its way in through physical or packaging modifications, side-channel exploits (i.e., power, analog, RF), and even maintenance or upgrade updates. The impact of these attacks on hardware is much more severe than software. With software, the impact can take hours or weeks fix but is usually corrected with a software update. Resolving the hardware may require that the entire IC be redesign and re-fabricated. This effort could take months and the company would suffer a major hit to its reputation and bottom line.
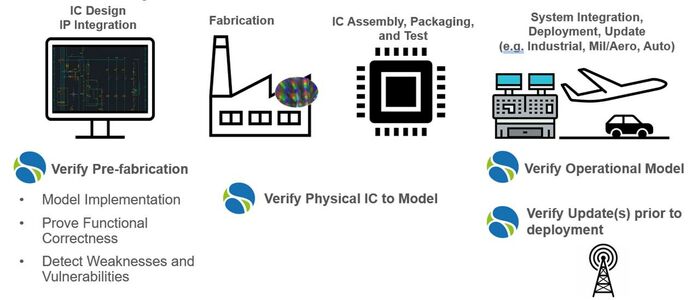
OneSpin can mitigate the risks of exploits throughout the hardware lifecycle by exhaustively verifying the absence of vulnerabilities. During IC design and IP integration, our trust technology models the implementation, proves the functional correctness of the design and detects weaknesses and vulnerabilities. During fabrication, IC assembly, and packaging, we can formally verify the physical IC to the model in a digital twin scenario. The model can be verified in the system during system integration and updates can be verified in isolation prior to deployment.
Our formal technology can also be leveraged to detect common weaknesses and vulnerabilities, check structural and functional dependencies, and identify added/changed functionality, hidden instructions and side channels.
Our trust capabilities can help assess IP trustworthiness to achieve signoff confidence. The technology can be used in a number of ways.
- Detect trigger logic to expose harmful threats early
- Identify reliability issues and remove unused logic early to eliminate later exploits and prevent excess power consumption
- Detect deadlock conditions to uncover potential denial-of-service holes
- List/sort vulnerabilities in a compact view and report identified issues
- Robust debugging with access to user-friendly source code and waveforms in a mature OS interface
The technology is part of an extensible platform where new categories and detection methods can be added.
There are many “bad actors” in the world today that thrive of exploiting products. Both intentional insertions and unintentional weaknesses or flaws are a means for exploitation. Running automated checks to identify known issues early and quickly can help to improve code and product quality and will reduce the risks of later exploits. Detecting if a product is “fit” for use is often difficult and time-consuming, but anything we can do today to start detecting potential holes early will save significant costs in later verification, minimize rerunning regressions tests or implementation steps, and prevent even worse, a recall or re-spin of an IC.