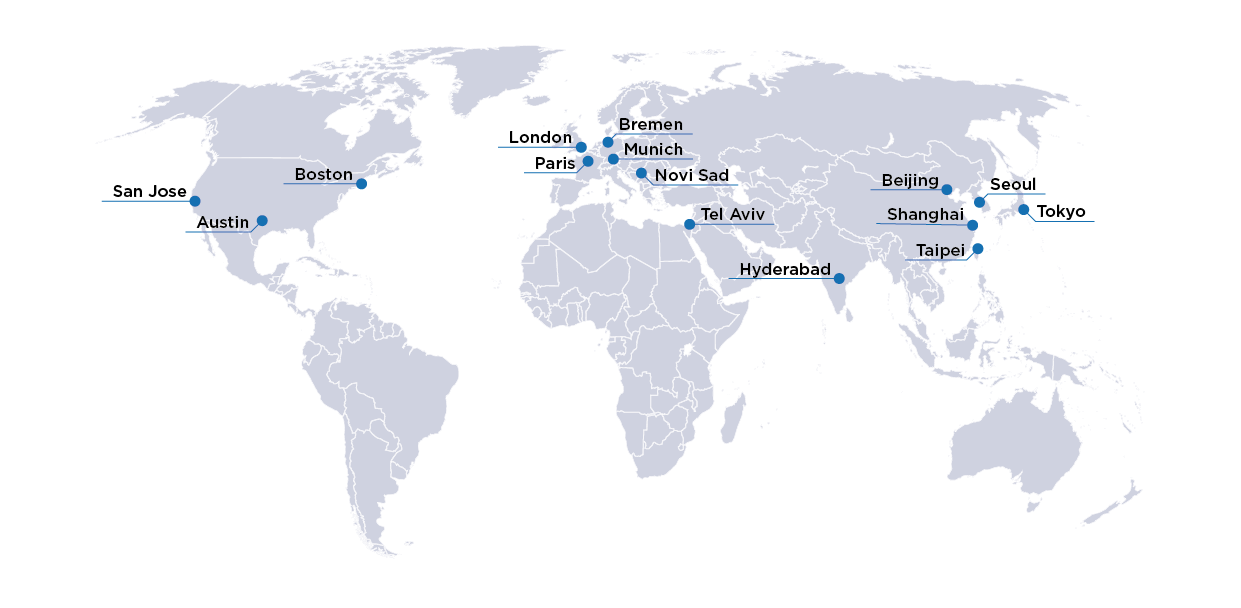
edaWorkshop20
Virtual Event | Register Online | October 7th & 8th
Join us at the upcoming edaWorkshop2020 on October 7th through the 8th! The event will host 10 sessions of RISC-V content including a session on RISC-V security moderated by OneSpin Solutions CEO, Dr. Raik Brinkmann.
Technical Marketing Manager, Sergio Marchese will be leading a discussion on:
"Security and Trust Assurance of RISC-V Open-source Cores RocketCore and OpenHW CV32E"
"RISC-V is leading the open-source hardware revolution. Individuals, companies, and not-for-profit organizations such as the Open Hardware Group are contributing RTL cores, simulators, toolchain software, and verification testbenches and results. Hardware security is crucial for a wide range of applications, from IoT to connected autonomous vehicles and other safety-critical systems. Open-source RISC-V cores offer both security challenges and opportunities. Processor cores provide fertile soil for the insertion of hardware Trojans. Complex pipeline implementations chasing performance, power, and area targets are a great hiding place for malicious logic, bugs, and unforeseen misuse cases. Pre-silicon RTL verification focuses on intended use cases and still misses bugs routinely. Malicious actors, on the other hand, may deliberately search for unintended behaviors and misuse cases exploitable in security attacks. Scrutiny from the broad engineering community can potentially provide a level of trustworthiness assurance that no proprietary core can match. This presentation reports on security and trust assurance contributions made for the open-source cores RocketCore and OpenHW CV32E. Using a RISC-V ISA model expressed in SystemVerilog and formal verification technology, the authors were able to detect and report security-relevant bugs and undocumented, non-standard functions."